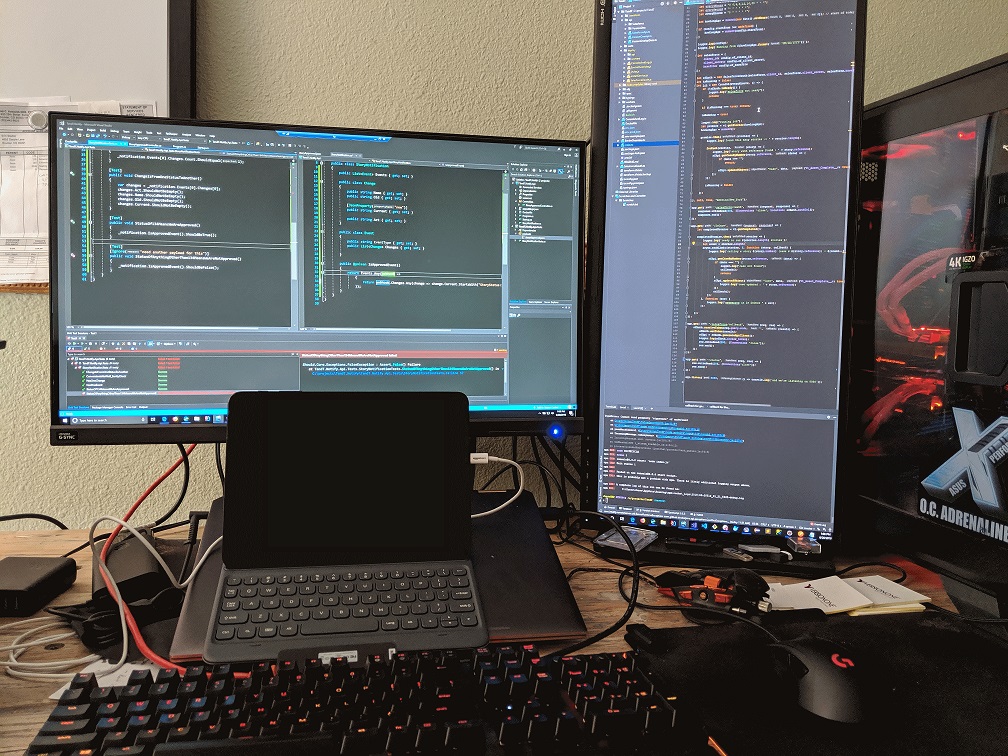
Skills Over Seats: Why You’re Botching Your New Transformation Strategy with AI this time

Blindly doing another form of "digital transformation" with the same patterns that have proven total failures? Here's how to make it good, make it stick, and make it happen.
AI Retired

AI is compressing the time to do things, as well as the need to "do it all yourself". So with that headspace, how will you become AI Retired?
The Path of Truth Tellers is Littered with Dead Scapegoats

What's your path look like? Because the Path of Truth Tellers is Littered with Dead Scapegoats.
Are You Parroting?
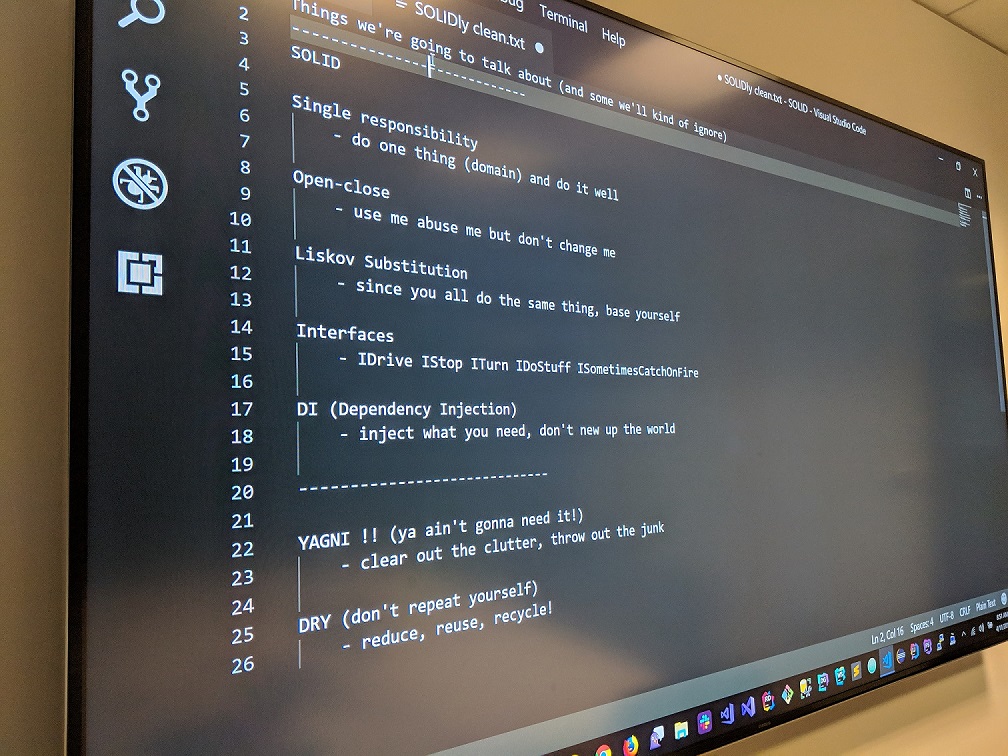
What's in that last book you've read? Is it something you've had to repeat during a meeting or 3? Do you really understand the concept... or are you parroting?
6 years.

Last month I had a number of instances where people and organizations I had worked with in the past had come full circle to what I had tried so hard to convey 6 years ago.
How do you price your product? A real example.

At some point, a price has to be set for a product. Here's a real-world example of how a company landed on a number.